Security Analyst Workflow
Although there is minimal configuration required in Security Analyst, you must give some thought and planning to create templates that lend themselves to good tagging practices. Before you start tagging within the Security Analyst Console, refer to Security Analyst Best Practices.
|
Within SLNX Management Console |
Within the Security Analyst Console |
||
|---|---|---|---|
|
|
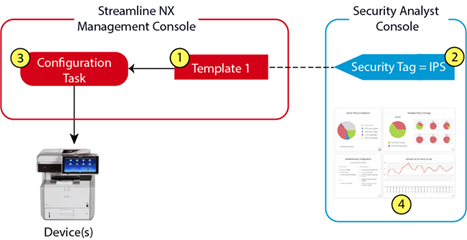
Create one or more configuration templates in SLNX that include security features. Create your template in: Read the Security Analyst Best Practices before you start. |
|
Apply one or more custom security tags to each template (as needed – only the templates that include security features). Refer to Add Tags to a Template Read the Security Analyst Best Practices before you start. |
|
|
Create a configuration task and apply the template to devices. Refer to Register a Template to a Task. Run the configuration task to apply the policy. Make sure the configuration task is completed before checking the device compliance status in Security Analyst Console. Run 'Refresh Data' manually or scheduled from Security Analyst so that the result of configuration tasks performed by SLNX will be reflected. |
|
View the compliance results in the Devices or Dashboards view. Refer to Security Dashboard. |
The diagram below depicts the workflow shown above, mapping the tasks that you must perform in Streamline NX vs those done in the Security Analyst console.
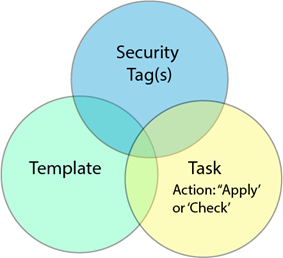
Once applied to a template, the tags track the status of a template at the device level. When a task is created that includes the tagged template, Security Analyst tracks the status of the template in terms of whether the template was successful applied (or checked), or if the task failed. The combination of a tagged template applied or checked within a task comprises the policy.
A policy is comprised of a template, one or more security tags, and a task that has run with either the ‘Apply’ or “Check” option.