Security Analyst Overview
You can view the dashboards in Security Analyst to determine the following:
-
Devices tagged with a security policy
-
Devices that are ‘in policy’ or ‘out of policy’, and when the state occurred
-
Template tags and the percentage of devices that are covered by the tag
-
Task failures that have caused a device to be out of policy
-
Historical data capturing device policy compliance over time
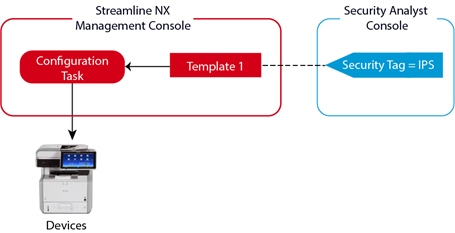
As an example, your company may want to establish an Intrusion Prevention System (IPS) policy that allows you to monitor servers and devices for IPS compliance (SSL/TLS, Enable HTTPs, etc.). Within the Streamline NX management console, you configure specific templates containing the IPS settings, and then create tasks to apply the templates to target servers and devices. Within Security Analyst, you then create and apply a custom IPS tag to the templates that contain the IPS settings. If you created a single template that contained all IPS settings, you would tag the template as shown in the image below. You could then easily track the status of the device in Security Analyst to ensure the IPS settings stay ‘in policy
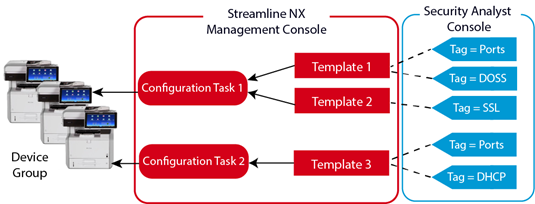
This is a simple diagram demonstrating the relationship between tasks, templates, and security tags.
However, this is a very simple example and the creation and distribution of templates among devices is typically far more complicated. For example, you are more likely to create multiple templates that contain the various IPS settings, whereupon you apply some templates to particular device and other templates to a different set of devices. When you start tagging in Security Analyst, your tagging becomes more complicated because your approach must be more specific, as shown below.